- Critical Thinking - Bug Bounty Podcast
- Posts
- [HackerNotes Ep.113] Best Technical Takeaways from Portswigger Top 10 2024
[HackerNotes Ep.113] Best Technical Takeaways from Portswigger Top 10 2024
We’re breaking down some of the best takeaways from PortSwiggers Top 10 of 2024. There’s some bangers in here!
Hacker TL;DR
This week we’re covering PortSwigger’s Top 10 Hacking Techniques of 2024! We chose 5 to put in this week’s HackerNotes, you can find the original page with all the posts here.
How to Hack AI + Masterclass: Rez0's been asked hundreds of times how to hack AI, and since he's an expert in this new field, he created a comprehensive post covering everything from how AI systems work to attack scenarios and jailbreaks. An AI hacking playbook fills a big gap in the sec community and he'll keep updating it as new techniques emerge.
And if you want to learn even more: he's hosting a 3-hour masterclass on March 11th at 12pm EST (9am PST).
If you're a Critical Thinker sub in our Discord, you get 50% off - basically pay $25 to save $100!
Hijacking OAUTH flows via Cookie Tossing: Cookie Tossing is when a subdomain sets cookies on its parent domain using headers or JavaScript. Browser cookies have key-value pairs and attributes, but only send the key-value to servers. The Domain attribute lets you control cookie access, by default, only the setting domain can access them, but using
Domain=.ctbb.showlets all subdomains use the cookie.Exploiting Cookie Tossing: If an attacker controls a subdomain, they can set parent domain cookies. This gets dangerous when they set session cookies for specific endpoints because the app might use the attacker's cookie instead of the victim's. Anti-CSRF tokens can stop this, but many JSON APIs skip them and rely on CORS instead. Apps using custom headers or Authorization are safe since browsers don't auto-submit these like cookies.
ChatGPT ATO - Wildcard Cache Deception: A critical cache deception vulnerability in ChatGPT led to account takeovers via exposed auth tokens. The issue comes from different URL encoding handling between Cloudflare and ChatGPT's web server. While Cloudflare wouldn't decode %2F..%2F (encoded slashes), the web server would, letting attackers trick the cache into storing sensitive API responses.
How it Worked:
ChatGPT's /share/ feature cached chat links
The CDN would cache anything under /share/
Using URL-encoded path traversal, attackers could store and retrieve other users' auth tokens
With these tokens, attackers could take over accounts, seeing chat history and billing info.
CVE-2024-4367 - Arbitrary JS Execution in PDF.js: A major XSS vulnerability was found in PDF.js, Firefox's default PDF viewer. Since many apps use this library, the impact was pretty big. The bug comes from how the library handles font rendering, it takes PDF data and directly runs it through JS eval(), letting attackers sneak in malicious code by crafting special font definitions.
Here's what an exploit looks like:
/FontMatrix [1 2 3 4 5 (0\\\\); alert\\\\('foobar')]If you're looking for new research topics, checking similar libraries could be a goldmine for vulnerabilities!
WorstFit: Unveiling Hidden Transformers in Windows ANSI: Orange explores how Windows handles text encoding between Unicode and ANSI. Through best-fit mappings, Windows tries to match Unicode characters to ANSI equivalents but often messes up. Characters like ¥ or \ can get misinterpreted, leading to security issues like path traversal or injection attacks.
Windows uses multiple encoding systems (UTF-16, UTF-8, and ANSI) for backwards compatibility and this creates problems when old code page systems interact with modern software. Take CVE-2024-4577 for example, when attackers used best-fit mapping to bypass PHP-CGI protections and inject commands. Similar issues affect tar, wget, and even Microsoft Excel.
Rez0's been asked hundreds of times how to hack AI, since he's really good at it and it's a new field that many people still don't understand. So he created a gigantic post detailing everything we need to know about the topic. It covers literally everything, from how they work to attack scenarios, jailbreaks and much more. If you're interested, go take a look at his post.
A playbook on AI was something that the hacking community was in need of, and he also told us that he’ll keep updating the post as new stuff comes up.
And if you're willing to the next step, he'll be hosting a 3-hour masterclass on March 11th at 12pm EST (9am PST). Learning from an AI master is an incredible opportunity! Btw, if you’re a Critical Thinker sub in our Discord you get a 50% discount on the masterclass. So yeah, pay $25 to get a $100 discount!
Every year, PortSwigger puts together a list of the Top 10 Web Hacking Techniques, voted by the community. This is the 18th edition, highlighting the craziest security research from the past year. This year, 121 research pieces were nominated, now that the final list is out, here are our top 5 picks from 2024’s best web hacking research:
Cookie Tossing lets one subdomain set cookies on its parent domain. Cookies can be set via the Set-Cookie header or JavaScript's Cookie API.
In browsers, cookies are stored as key-value-attribute tuples. When sent to servers, only the key and value are included, not the attributes, browsers also limit how many cookies a domain can have.
The Domain attribute controls which domains can access a cookie. By default, cookies are only accessible to the domain that set them. Using Domain=.ctbb.show makes a cookie accessible to all subdomains of ctbb.show. Parent domains can set cookies for all subdomains but can't target specific ones.
The Path attribute limits which URLs can use the cookie. By default, cookies are available to the path that created them and its subdirectories. Cookies with more specific paths (like /account/settings) are sent before less specific ones (like /account), ensuring the most specific cookie takes priority when multiple match.
- Exploiting Cookie Tossing
When an attacker controls a subdomain (through XSS or by design), they can set cookies on the parent domain. This becomes dangerous when they set their session cookie on the victim's browser for specific endpoints.
For example, an attacker sets a cookie with Domain=.ctbb.show and Path=/episodes/113. The victim uses the app normally, but when they access certain API endpoints the app uses the attacker's cookie instead.
Apps using anti-CSRF tokens can block it since the request includes the victim's token, not the attacker's. Despite this, many apps remain vulnerable because JSON-based APIs often skip anti-CSRF protection, relying instead on Same Origin Policy (SOP) and CORS. When devs rely only on CORS preflights and skip CSRF tokens, endpoints become exposed to cross-subdomain attacks. On the flip side, apps using custom headers or Authorization headers for sessions are safe from cookie tossing, since browsers don't automatically submit these like they do with cookies.
A critical cache deception vulnerability in ChatGPT led to account takeovers by exposing authentication tokens.
By leveraging path traversal and URL parser confusion, it was possible to manipulate Cloudflare’s CDN caching rules. The vulnerability stemmed from the way Cloudflare and the ChatGPT web server handled URL encoding differently. Cloudflare would not decode %2F..%2F (encoded slashes), while the web server would. This allowed an attacker to trick the cache into storing API responses containing user auth tokens.
How it Worked:
The /share/ feature cached user-shared chat links.
The CDN would cache anything under /share/, even if it didn’t exist.
By using a URL-encoded path traversal (%2F..%2Fapi/auth/session), an attacker could force the cache to store sensitive API responses.
Once stored, the attacker could retrieve another user’s auth token by visiting the same cached URL.
With the leaked auth token, attackers could take over accounts, access chat history, and view billing details.
This was covered in HN72 by @gr3pme, so here it is:
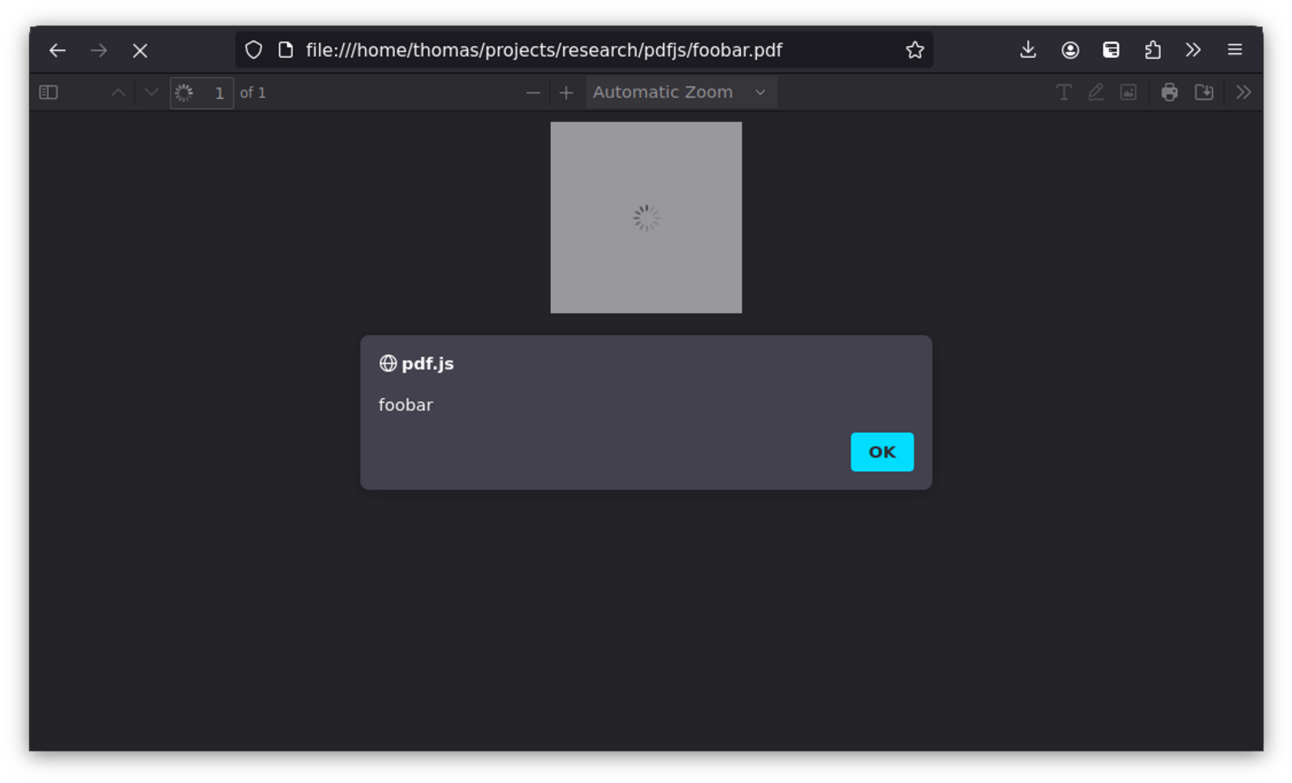
Sound the XSS Klaxxon - a big XSS has dropped affecting PDF.js, a JS-based PDF viewer from Firefox. This also happens to be the default PDF viewer for Firefox users, so it’s a pretty widespread XSS.
The library is quite popular, so this will also affect quite a few web and desktop applications that depend on the library.
The TL;DR of the vuln is due to the way the library performed glyph rendering. It would take apart the PDF file and place it directly into JS, and subsequently eval it. This means you could specify a font, close off the call and place your JS payload in to execute. Example from the PDF:
/FontMatrix [1 2 3 4 5 (0\\\\); alert\\\\('foobar')]
Which would result in the XSS popping in the document, as shown below:
Auditing libraries and functionality similar to this provide an incredibly rich attack surface if you’re looking for a new research avenue.
Researcher @paulosyibelo discovered a clever trick to harvest double-clicks from users on sensitive functionality. Dubbed "DoubleClickjacking," it's explained simply as:
DoubleClickjacking is a new spin on the classic clickjacking attack that uses a double-click sequence instead of a single click. This small change bypasses all known clickjacking protections, including X-Frame-Options headers and SameSite cookies. The technique affects almost every website and has led to account takeovers on major platforms.
The attack works through these timing and event order tricks:
An attacker creates a webpage with a button that opens a new window.
When the user clicks this button:
A new window appears on top, prompting the user to "double-click."
This window immediately changes the parent window's location to the target page.
The parent window now loads the target page (like OAuth authorisation), while the top window still shows the double-click prompt.
When the user double-clicks:
The first click closes the top window.
The second click lands on the now-exposed authorisation button below.
The user unknowingly authorises the attacker's application with their account.

The impact of this attack depends entirely on the functionality being targeted. It's especially effective for tricking users into actions that could lead to account takeovers. The research highlighted several high-value targets, including OAuth flows and one-click account changes.
Clickjacking often gets dismissed because demos lack impact. But this research proves it can be devastating when paired with the right functionality!
They successfully compromised Salesforce, Slack, and Shopify, achieving one-click account takeovers on all three!
Check out the full writeup and the exploit POC here: https://www.paulosyibelo.com/2024/12/doubleclickjacking-what.html#:~:text=Proof of Concept (PoC) Code
This research by @Kevin_mizu was recently featured on the pod and it's probably (at least we hope) fresh in everyone's mind, so we're not going to cover it here—just throwing it in as a bonus!
The research is linked in the title above, and you can also read the HackerNotes here.
Orange explores how Windows handles text encoding when converting between Unicode and ANSI. Through best-fit mappings, Windows tries matching Unicode characters to ANSI equivalents but sometimes messes up. Characters like ¥ or \ can get misinterpreted, leading to serious security issues like path traversal or injection attacks.

Windows juggles multiple encoding systems (UTF-16, UTF-8, and ANSI) to maintain backwards compatibility. This creates dangerous edge cases when older code page systems interact with modern software. A notable example is CVE-2024-4577, a bypass for an older PHP-CGI exploit where attackers used best-fit mapping to inject commands. Beyond PHP, programs like tar, wget, and Microsoft Excel are similarly vulnerable.
Attack surfaces include filenames, paths, environment variables, and command-line arguments. If an application uses ANSI APIs in Windows, it's likely exploitable. Affected software spans from open-source tools like curl and PostgreSQL to Microsoft Excel. The issue? They all use ANSI functions that mishandle character conversions.
Orange recommends abandoning ANSI APIs for Unicode ones, properly validating inputs, and using UTF-8 whenever possible. Users should configure their systems to prefer UTF-8. Windows' legacy support is a double-edged sword, keeping old programs running while introducing these vulnerabilities.
That's a wrap for this week’s HackerNotes!
And as always, keep hacking!